👋 Welcome to Unlocked
Most breach stories start the same way: a vulnerability, a misconfiguration, an exposed server.
But Scattered Spider doesn’t need any of that.
They’re one of the most disruptive threat groups in the world right now because they specialize in something harder to patch: human trust.
This isn’t a group that “breaks in.”
They talk their way in — then move fast, hit identity systems, and trigger chaos.
If you’re a CISO, IT leader, or security practitioner, this is one of the groups you should be planning for specifically.
🕷️ Who is Scattered Spider?
Scattered Spider (also tracked under multiple names like UNC3944 and Octo Tempest) is known for:

They’re especially dangerous because they don’t need deep technical exploits to win.
They just need:
one person to trust them
one workflow to fail
one reset request approved
🎯 Why CISOs Care: Their Target is Your Identity Layer
Scattered Spider often goes after:
1) The Help Desk
They’ll impersonate employees and pressure support teams into:
password resets
MFA resets
device enrollment
account recovery
Translation: they attack the “emergency doors” you built for productivity.
2) Identity Providers (Okta, Entra ID, etc.)
Once they control identity, they control everything:
SaaS apps
internal systems
VPN
cloud resources
admin tools
3) Privileged Access
They move fast to:
escalate permissions
create persistence
add new MFA devices
create new accounts / tokens
🧠 Their Playbook (Simplified)
Here’s the pattern security teams keep seeing:
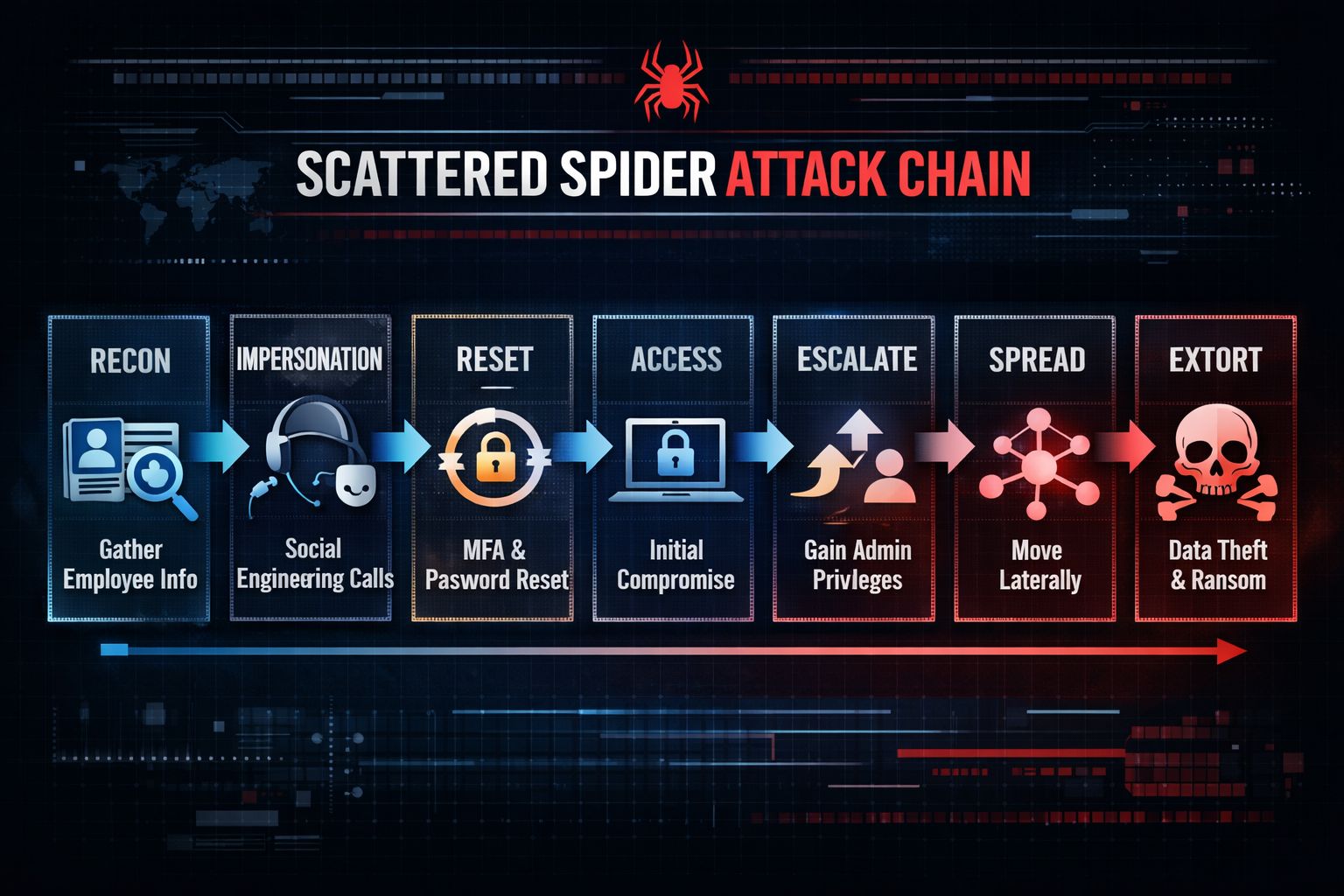
More specifically:
Collect employee details (LinkedIn, breached data, OSINT)
Call the help desk pretending to be the employee
Push urgency (“I’m locked out, I’m traveling, I have a board meeting”)
Get MFA reset / password reset approved
Log in and enumerate apps
Target admin roles and security tools
Move laterally + steal data
Deploy ransomware or extort without encryption
🚨 Signs You’re Being Targeted (Early Warning Signals)
These are the “small anomalies” that show up before the big breach:
Identity & Access Red Flags
multiple MFA reset requests in a short window
password resets followed by logins from unusual devices
repeated “failed push” attempts (fatigue patterns)
new device enrollment right after an HR/IT request
Help Desk Red Flags
employees claiming “lost phone” repeatedly
requests that bypass normal ticket workflows
callers refusing to verify through standard steps
requests timed during shift changes or weekends
Admin & SaaS Red Flags
new OAuth app approvals that weren’t planned
new mailbox forwarding rules
suspicious access to SSO settings / identity logs
new privileged roles assigned unexpectedly
🛡️ How to Defend Against This Group (Practical Controls)
✅ 1) Harden the Help Desk (This is the front door)
If your help desk can reset access, it needs security controls like:
mandatory call-back verification
out-of-band confirmation (not the same email they’re trying to access)
step-up verification for MFA resets (manager approval, HR verification, etc.)
flag high-risk users (finance, execs, IT admins)
Pro move: treat help desk workflows as part of your identity security perimeter.
✅ 2) Lock Down MFA Resets + Enrollment
MFA is only strong if attackers can’t replace it.
Protect:
new authenticator enrollments
device re-registration
phone number changes
recovery methods
Require:
approval workflows
risk-based controls
time delays for high-risk changes
✅ 3) Monitor for “Identity Takeover Patterns”
If you have detection engineering capacity, prioritize alerts for:
MFA reset → new login within minutes
new device enrollment → privileged role access
repeated password resets across multiple users
login success after multiple failed attempts from different IPs
✅ 4) Reduce Blast Radius with Least Privilege
Scattered Spider wins when one compromised user can reach too much.
Limit:
standing admin access
shared accounts
over-permissioned SaaS roles
“everyone can install apps” policies
🧨 Why This Keeps Working (Even at Mature Companies)
Because it exploits something security teams rarely model correctly:
Your people are part of your authentication system.
If your identity stack is perfect but your recovery workflow is weak…
your org is still vulnerable.
👀 Threat Groups to Watch (Quick CISO Cheat Sheet)
Here are additional threat actors worth tracking because they’re shaping what “modern attacks” look like:

💡 Unlocked Tip of the Week
Run a “Help Desk Breach Drill” — Not a Phishing Test
Most orgs test employees with phishing simulations.
This week, test something attackers actually exploit:
Your identity recovery workflow.
📊 Poll of the Week
Which part of identity security is your biggest risk right now?
🔥 Final Takeaway
Scattered Spider is a reminder that the next era of cyber risk isn’t always “more advanced malware.”
Sometimes it’s a better phone call.
If your organization hasn’t hardened help desk identity verification, MFA reset workflows, and identity telemetry…
This is the group that will prove why it matters.
Stay ready. Stay resilient.
Until next time,
Meet Jordan Hale - Software Developer
Jordan Hale works on backend systems, automation, and reliability tooling that support secure access and modern infrastructure. With experience across cloud-native development and security-focused engineering, Jordan helps improve telemetry, strengthen authentication workflows, and support incident response teams with clearer, more trustworthy data.
Jordan is passionate about practical security engineering and enjoys exploring how automation and AI can reduce operational risk and speed up detection. With an engineering-first mindset, Jordan focuses on clean implementation, measurable outcomes, and strong operational discipline.
About Our Sponsor
Introducing the first AI-native CRM
Connect your email, and you’ll instantly get a CRM with enriched customer insights and a platform that grows with your business.
With AI at the core, Attio lets you:
Prospect and route leads with research agents
Get real-time insights during customer calls
Build powerful automations for your complex workflows
Join industry leaders like Granola, Taskrabbit, Flatfile and more.


