👋 Welcome to Unlocked
Ransomware is often described as a “lock-and-pay” problem — malware encrypts files, the business panics, and a ransom demand follows.
But in 2026, ransomware isn’t really about encryption anymore. It’s about leverage. It’s about controlling timelines, manipulating decision-makers, and forcing organizations into high-stakes choices under pressure.
A modern ransomware incident doesn’t just disrupt IT. It triggers legal exposure. It pulls executives into crisis mode. It turns customers into skeptics. It creates uncertainty that spreads faster than the malware itself.
This week, we’re exploring a more uncomfortable truth: ransomware has evolved into a business model built on human behavior, not just technical compromise.
Let’s break it down.
🧨 Ransomware Has Become “Leverageware”

The old ransomware story was simple: encrypt systems → demand payment → provide a key.
The 2026 version is more strategic: gain access → map pressure points → threaten what matters most → force urgency.
Double and triple extortion playbooks are now the norm — data theft, disruption, and pressure tactics layered together.
This shift also fits the broader intrusion patterns tracked in the Verizon DBIR.
🧠 The Real Target: Leadership Psychology
Ransomware isn’t won in the malware stage — it’s won in the meeting room.
Attackers know leadership fears:
liability
exposure
public trust
losing control of the story
That’s why ransomware planning increasingly overlaps with governance frameworks like the NIST Cybersecurity Framework.
And why incident disclosure expectations keep rising for public companies.
🕳️ Quiet Ransomware Is the Most Dangerous Ransomware
The worst ransomware events often start quietly:
a suspicious login
a “normal” helpdesk request
a stale contractor account
an over-permissioned admin role
Many groups sit inside environments first, staging access and identifying leverage before detonating disruption. MITRE ATT&CK is a great reference for the techniques behind this.
More guidance for practical prevention + response from CISA.
🧬 Extortion Now Hits the Whole Ecosystem
In 2026, ransomware pressure often spreads beyond the victim company — toward customers, partners, and vendors.
That’s why third-party risk and supply chain exposure are now ransomware multipliers, not “extra credit.”
And why “secure by design” is becoming a stronger expectation, not just a slogan.
🪪 Identity Is Still the Fastest Path to Ransomware
Most ransomware stories still follow a familiar arc:
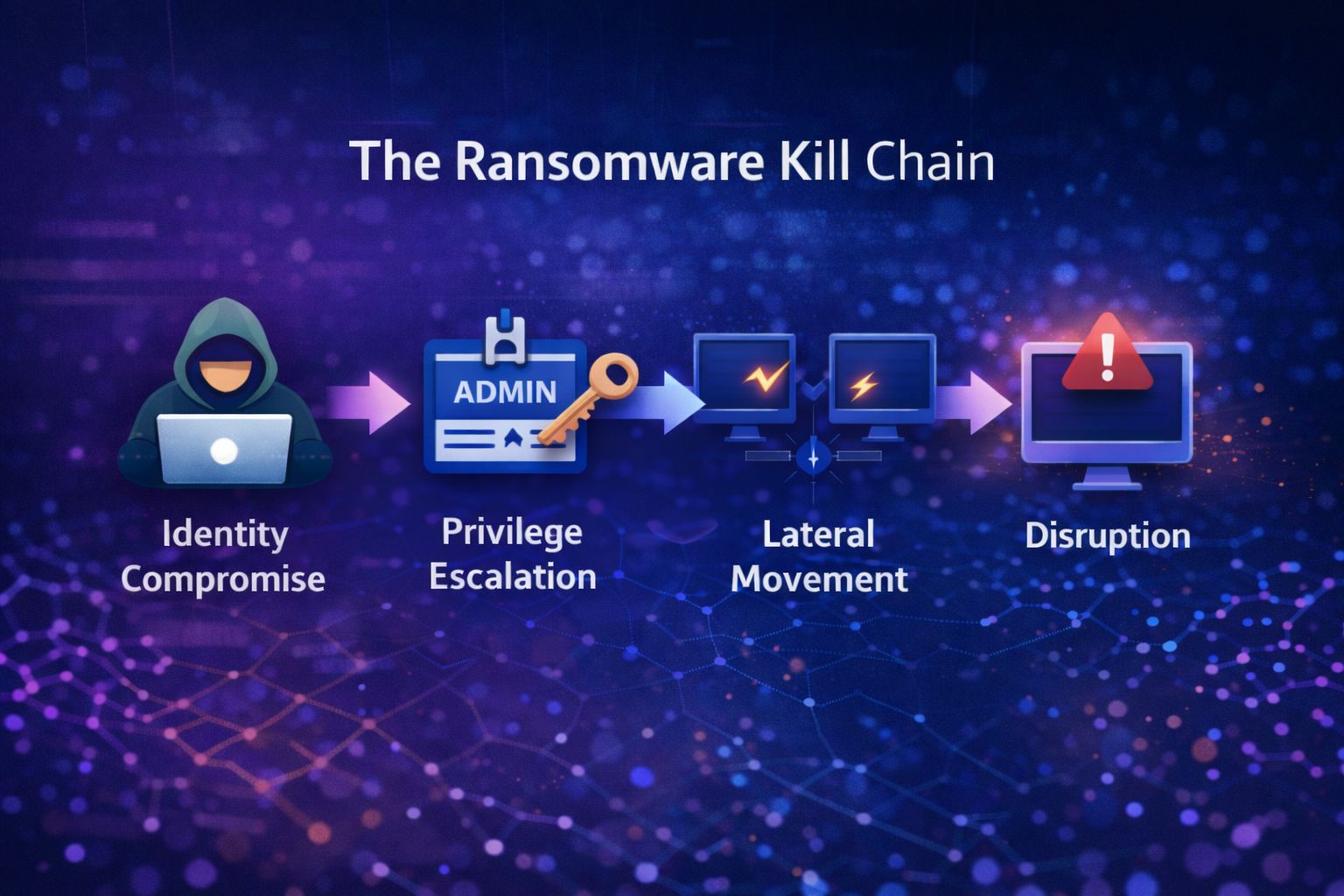
It’s not always advanced hacking — it’s often credential misuse and access sprawl.
Microsoft’s security resources are also strong for identity defense best practices.
🧾 Disruption Is the Product Now
Leaders don’t get to ignore fear — because executives, regulators, and customers won’t.
But they absolutely can’t build strategy on fear alone.
Instead, they need to:
translate anxiety into architecture
ground decisions in evidence, frameworks, and outcomes
build resilience while steering narrative responsibly
Useful guiding frameworks include:
NIST Cybersecurity Framework
https://www.nist.gov/cyberframeworkCISA Secure by Design
https://www.cisa.gov/securebydesign
Boards need clarity, not adrenaline.
Teams need direction, not panic.
Leadership is the difference.
🔎 So What Should CISOs and IT Leaders Do?
The key shift in 2026: response readiness is a competitive advantage.
Strong programs focus on:
identity + privileged access control
recovery confidence (not hope)
clear crisis ownership (IT, legal, PR, execs)
practiced response playbooks
Start here for practical resources: CISA stop ransomware & NIST cyber framework.
💡 Unlocked Tip of the Week
Ask this before the next incident:
“If we lost identity tomorrow, could we still run the business?”
If not, you don’t just have a security gap — you have a ransomware leverage problem.
📊 Poll of the Week
What are ransomware groups optimizing for most in 2026?
🙋 Author Spotlight
Meet Samuel Ortiz - Junior Platform Engineer
Samuel Ortiz works on platform automation, event logging, and backend systems that support modern identity architectures. With a background in Python, Go, and cloud-native tooling, he helps maintain telemetry pipelines, improve log reliability, and support incident analysis teams with better data quality.
Samuel is passionate about security automation and enjoys exploring how AI and machine learning can improve detection workflows. He brings a practical, engineering-first mindset, focusing on clean implementation and strong operational discipline.
✅ Wrapping Up
Ransomware in 2026 isn’t just a technical attack — it’s a leverage strategy.
Encryption is only one weapon.
The real weapon is pressure, uncertainty, and control of the timeline.
Stay ready. Stay resilient. Stay calm under pressure.
Until next time,
About Our Sponsor
Help us make better ads
Did you recently see an ad for beehiiv in a newsletter? We’re running a short brand lift survey to understand what’s actually breaking through (and what’s not).
It takes about 20 seconds, the questions are super easy, and your feedback directly helps us improve how we show up in the newsletters you read and love.
If you’ve got a few moments, we’d really appreciate your insight.
1


