Introduction
Multi factor authentication has become a foundational element of modern access systems. It is a key component in access control, as modern access control systems regulate entry to secure resources by using multiple verification methods such as physical credentials, biometric verification, and location-based factors. As digital identities have expanded across devices, applications, and cloud environments, the need to verify user identity through more than a password has steadily increased.
The evolution of multi factor authentication has been driven by the need for heightened security in response to rising cyberthreats. From early banking systems to biometric authentication and behavioral biometrics, MFA reflects how security measures adapt as technology and risk change over time.
Understanding the history of multi factor authentication helps explain why it is now considered essential for protecting private data, reducing identity fraud, and enabling secure access across digital systems.
History of Multi Factor Authentication
Early digital systems in the 1960s and 70s utilized basic password systems that were easily compromised. At the time, computing environments were limited, and identity verification focused almost entirely on a single factor. These authentication methods were implemented in early data transmission systems to enhance security during data exchanges.
The earliest use of multi factor authentication dates back to early ATMs, which required a physical card and a PIN to access accounts. The first ATMs debuted in 1967 in London and in 1969 in New York, requiring both a physical card and a PIN. This combination of possession and knowledge factors laid the groundwork for modern authentication concepts.
MFA and its predecessor two factor authentication have been with us in various forms for over twenty years. The origins of modern 2FA include patent disputes in the mid 1990s over competing technologies focused on combining passwords with hardware tokens. There is ongoing debate over who invented two factor authentication, with Kim Dotcom claiming to have invented it in 1997, while AT&T held a relevant patent from 1995. These developments were significant in shaping the evolution of authentication methods and improving account security.
Multi Factor Authentication Takes Shape
Multi factor authentication requires the use of two or more distinct types of evidence to verify a user’s identity. MFA typically verifies a person’s identity using three factors: something you know, something you have, and something you are. The addition of a second factor — such as combining a password (knowledge) with a code from an authentication app (possession) — significantly increases security by making it much harder for attackers to gain unauthorized access.
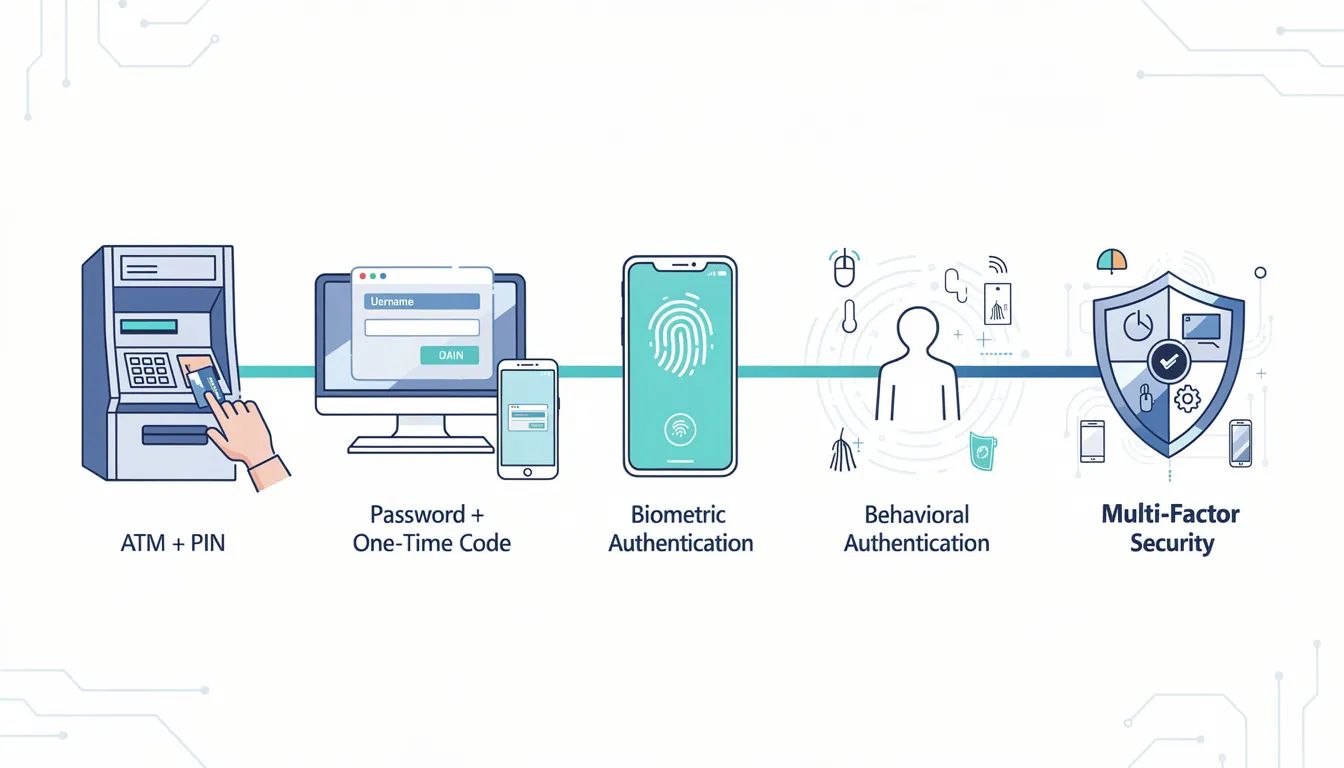
Knowledge factors in MFA include passwords or answers to security questions, which are something only the user knows. Possession factors in MFA include security codes generated by an authentication app or received via SMS, which are something only the user has. Inherence factors in MFA are biometric methods, such as fingerprint or facial recognition, which are something the user is.
As systems became more connected, factor authentication moved from physical environments into online systems.
Authentication Factors and Early Online Security
The 2000s saw the rise of multi factor authentication as a response to increasing data breaches and the need for stronger security measures. As identity theft and identity fraud increased, organizations realized that passwords alone could not protect user accounts.
This period marked the widespread use of MFA technologies, as organizations sought to strengthen security and protect sensitive information.
Banking institutions began rolling out MFA for online customers around 2004 as online banking became prevalent. Authentication codes delivered via text message or hardware token became common for verifying identity during the login process. Users are only granted access after successfully providing the required authentication factors, ensuring that only authorized individuals can enter the system.
SMS based codes and TOTP apps made MFA more accessible in the 2000s, reducing friction for end users.
Types of Authentication
Authentication is the cornerstone of online security, ensuring that only authorized users gain access to sensitive systems and data. There are several authentication methods used to verify user identity, each relying on different authentication factors. Multi factor authentication (MFA) enhances security by requiring multiple authentication factors before granting access. These factors typically fall into three categories: knowledge (something you know, like a password), possession (something you have, such as a mobile device or a code sent via text message), and inherence (something you are, like biometric authentication using fingerprint scanning or facial recognition).
Two factor authentication (2FA) is a widely used form of MFA that combines two distinct authentication factors, such as a password and a one time password (OTP) generated by an authenticator app or sent via text message. Biometric authentication, including fingerprint scanning and facial recognition, leverages unique physical characteristics to verify user identity, making it much harder for unauthorized users to gain access. By combining multiple authentication factors, organizations can significantly strengthen their security posture and protect against unauthorized access, identity theft, and data breaches.
Online Security and the Smartphone Era
The evolution of multi factor authentication accelerated in the mid 2000s, when smartphones first began making a splash with consumers. MFA gained popularity in the digital era as technological advancements and increased consumer adoption made it more accessible and user-friendly. The broad adoption of MFA as a security staple is closely tied to the mobile device explosion, which played a crucial role in its evolution.
MFA became more appealing to consumers as smartphones provided convenient methods for receiving authentication codes via SMS or email. The introduction and mass adoption of smartphones have significantly reduced the friction users experience during authentication.
The use of mobile phones has facilitated the adoption of MFA by allowing users to receive one time passwords or authentication codes easily.
From Hardware Tokens to Software Tokens
Before smartphones, hardware token devices were widely used. These devices generated authentication codes and served as possession factors in MFA systems.
Smartphones enabled a shift from hardware tokens to software based MFA solutions in the early 2010s. Authenticator apps like Google Authenticator replaced SMS codes, generating time sensitive codes on smartphones without relying on cellular networks.
This shift made MFA easier to deploy and manage across large user populations.
Biometric Authentication Enters the Mainstream
Biometric authentication marked a major shift in identity verification. Fingerprint scanning, facial recognition, and voice recognition introduced inherence factors that were more difficult to steal or replicate. Biometric authentication is considered one of the most secure authentication methods available, contributing significantly to the evolution of multifactor authentication.
Apple’s Touch ID and Face ID brought biometric authentication to the mainstream in the 2010s. These technologies familiarized end users with biometric factors as part of everyday access.
Biometric authentication strengthened user authentication while improving convenience across mobile devices.
Behavioral Biometrics and Adaptive Authentication
The future of multi factor authentication is expected to include more sophisticated biometrics and behavioral authentication methods. Behavioral biometrics, which analyze user interaction patterns, are becoming a key trend in multi factor authentication.
Typing biometrics is emerging as a user friendly method for multi factor authentication that does not require additional hardware. Behavioral biometrics analyze typing patterns, device usage, and interaction timing to verify identity continuously.
Modern MFA systems utilize contextual factors like geolocation and device type to adjust security requirements. Advanced MFA systems analyze context such as location and behavior to adapt security requirements dynamically.
The integration of behavioral authentication with traditional MFA methods is expected to enhance security while providing a frictionless user experience.
Multifactor Authentication and Data Breaches
MFA significantly reduces the likelihood of account compromise compared to single factor authentication methods. However, MFA is not a silver bullet for security and can still be ineffective against modern threats like malware and social engineering. Private individuals, as well as organizations, are vulnerable to cyber threats and benefit from the protection offered by MFA.
Multi factor authentication is vulnerable to phishing attacks, which can compromise user credentials even when MFA is in place. MFA can be bypassed through SIM swapping, where attackers gain control of a victim’s phone number to intercept authentication codes.
MFA fatigue attacks occur when attackers bombard users with multiple authentication requests, hoping they will eventually accept one.
Certain MFA methods, such as SMS based verification, are criticized for their security weaknesses, including the risk of interception.
Identity Fraud Prevention
In an era where identity fraud is a persistent threat, multi factor authentication stands out as a powerful defense. By requiring multiple authentication factors, MFA makes it significantly more challenging for hackers to impersonate users and gain access to sensitive information. Advanced authentication methods, such as behavioral biometrics, analyze unique user behaviors — like typing patterns or voice recognition — to verify user identity and detect suspicious activity. These behavioral authentication methods add an extra layer of security by continuously monitoring for anomalies that could indicate identity fraud.
Adaptive authentication further enhances protection by dynamically adjusting security requirements based on user behavior and risk factors. For example, if a login attempt is made from an unusual location or device, the system may require additional authentication steps. By integrating behavioral biometrics and adaptive authentication with traditional MFA, organizations can better safeguard user identities, prevent unauthorized access, and reduce the risk of identity fraud and data breaches.
MFA Adoption and Regulation
Regulatory compliance has significantly driven the adoption and evolution of multi factor authentication. Many regulations and industry standards now require MFA implementation, with failure to comply resulting in financial, legal, and operational penalties.
In the United States, regulations like CCPA and HIPAA require appropriate authentication controls, including MFA. The General Data Protection Regulation in the European Union requires organizations to implement appropriate security measures, including MFA, to protect personal information.
Industry standards like the Payment Card Industry Data Security Standard require financial institutions to use MFA to secure access to systems handling payment information.
Legislation, regulations and industry guidelines, including PCI DSS 4.0, PSD2, HIPAA and the updated NIST SP 800 63B 4, align on requiring stronger MFA and continuous session monitoring.
MFA has become an essential tool in any company's cybersecurity toolkit, with cybersecurity insurance providers requiring its adoption.
MFA Adoption in Modern Organizations
MFA adoption has accelerated rapidly, with over 90 percent of enterprises using some form of MFA today. MFA adoption has accelerated rapidly, with over 90 percent of enterprises using some form of MFA today, compared to just 20 to 30 percent in 2020.
Cloud technologies, enterprise mobility, and the increased use of bring your own device policies solidified the positive trend in MFA implementation. Remote work further accelerated MFA adoption as secure access to private data became critical.
Remote Work Security
With the rise of remote work, ensuring secure access to company systems and sensitive data has become more important than ever. Multi factor authentication is a critical security measure for remote work environments, providing an essential barrier against cyber threats and identity fraud. Employees can use mobile devices to receive authentication codes, push notifications, or one time passwords, making it easy to verify user identity from anywhere. Biometric authentication methods, such as fingerprint scanning and facial recognition, offer additional security by confirming the user’s unique physical traits.
To further protect sensitive information, organizations often implement additional security measures like virtual private networks (VPNs) and encryption, ensuring that data transmission remains secure even outside the office. By combining multi factor authentication with these security measures, companies can provide remote workers with secure access to business systems while minimizing the risk of data breaches, unauthorized access, and identity theft. This layered approach to security helps organizations adapt to the evolving landscape of remote work and sophisticated cyber threats.
Passwordless Authentication and the Future
Passwordless authentication standards like FIDO2 and WebAuthn are designed to eliminate passwords entirely. Standards like FIDO2 and WebAuthn allow for cryptographic authentication without traditional passwords.
Experts anticipate that AI and machine learning will play a significant role in the future of MFA by enhancing adaptive authentication and anomaly detection.
As MFA continues to evolve, the focus is shifting toward access that feels seamless while still maintaining strong identity verification.
This is where approaches centered on presence and proximity, like those used by EveryKey, quietly fit into the evolution of MFA. By continuously confirming identity based on presence rather than repeated prompts, modern access systems reduce friction while maintaining confidence in user identity.
Conclusion
The history of multi factor authentication reflects the changing nature of identity, risk, and access. From early ATMs to behavioral biometrics and adaptive authentication, MFA has evolved to meet increasingly sophisticated cyber threats.
As identity fraud, phishing attacks, and data breaches continue to rise, MFA remains a critical part of secure access. The future of authentication will prioritize continuous identity confirmation, reduced reliance on passwords, and access systems that balance security with simplicity.
FAQ: History of Multi Factor Authentication
When was multi factor authentication first used?
The earliest use dates back to ATMs in the late 1960s, which required both a card and a PIN.
Why did MFA become popular in the 2000s?
Rising data breaches, online banking, and identity theft drove the need for stronger authentication.
Is MFA still effective today?
Yes, MFA significantly reduces account compromise, though it must be implemented correctly.
What role do smartphones play in MFA?
Smartphones enabled software tokens, authenticator apps, and biometric authentication.
What is the future of MFA?
The future includes behavioral biometrics, adaptive authentication, and passwordless access models.
